FIREWALL IN LINUX
A Firewall is one of the most fundamental ways to monitor & filter incoming and outgoing traffic in the secured networks.
A set of inbound and outbound rules are defined within firewall settings to determine which traffic to is allowed or blocked.
Zones in firewalld :-
Trusted:
It is used for the Highest level of trust. It Allow incoming and outgoing traffic to all the machines in this network.
Home:
For home networks. Trust all the other machines on the network. It allows only a few incoming connections.
Work:
For work environments. Trust all machines, and allow only approved incoming connections.
External:
It is configured when we are using firewall as a gateway. NAT masquerading is used to ensure that the internal network topology is hidden, but the servers are still reachable.
Public:
Trust no-one by default. Allow a handful of incoming connections, based on need.
Drop:
Lowest trust level. Drop every incoming packet without replying. Only allow outgoing traffic.
Runtime vs permanent settings in firewalld
Firewalld allows you to define two kinds of settings: runtime and permanent. Runtime is the currently running configuration, which is reverted to the permanent configuration-set upon reboot.
By default, when you use firewall-cmd to configure your firewall, the changes are made to the runtime configuration set. To make changes permanent, you can add the --permanent option to the command.
Prerequisites
CentOS 8 server and A user with sudo privileges.
Install and enable firewalld
[root@ait~]#yum list installed | grep firewalld
[root@ait~]#yum install firewalld
[root@ait~]#systemctl enable firewalld
[root@ait~]#reboot
Verify that firewall is running
[root@ait~]#firewall-cmd --state
Get to know the defaults
[root@ait~]#firewall-cmd --get-default-zone
You should see that public is set.
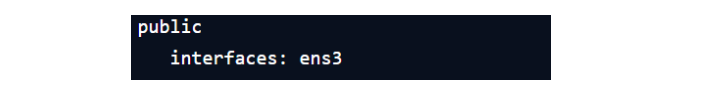
Display Active zones
[root@ait~]#firewall-cmd --get-active-zone
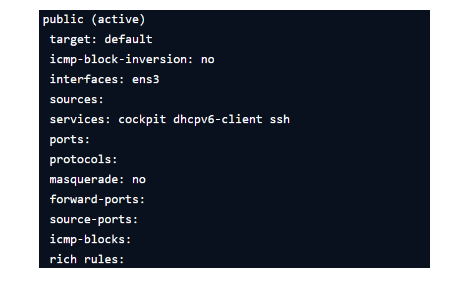
Display all rules applicable to the Public zone
[root@ait~]#firewall-cmd –list-all
Show other available zones
#firewall-cmd --get-zones
block dmz drop external home internal libvirt public trusted work
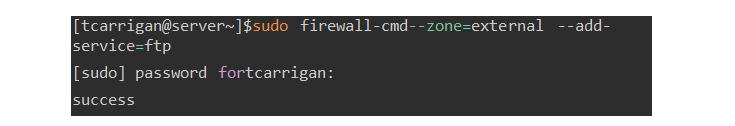
Allow or deny by service
#firewall-cmd --zone=external --add-service=ftp
Example :
#firewall-cmd --reload
success
#firewall-cmd --permanent --zone=external --add-service=ftp
Allow or deny by Port number
Allow traffic over non standard port using following method-
#sudo firewall-cmd --permanent --zone=external --add-port=60001/udp
Success
Result -
#sudo firewall-cmd --zone=external --list-ports
60001/udp
Remove recently added firewall rule-
#sudo firewall-cmd --permanent --zone=external --remove-port=60001/udp
Success